I was given this receipt at one of the shops in Gloucester. The owner of this shop puts her network at risk by conducting all her business activities, however small, from under the superuser account. It may only take a dozen of seconds for an intermediate level opportunist hacker to set up a backdoor while their friend is distracting the cashier – and then hack into the shop computer and arrange a whopping 99%-off sale for them and their friends.
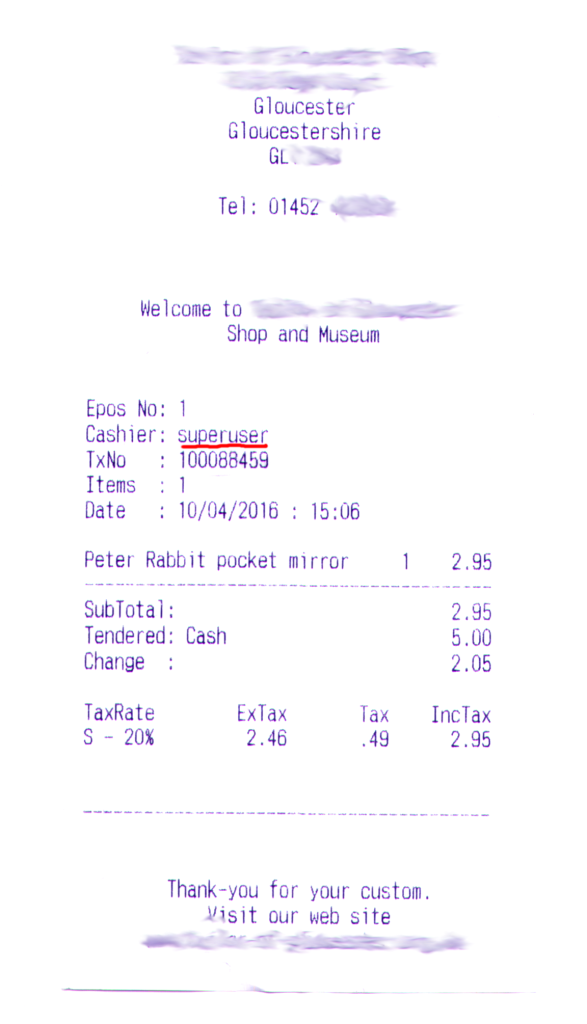
Negligence towards proper access rights management is one of the most common causes for security breaches. While other data protection instruments, such as encryption, backup routine, or firewalls, are ‘touchable’ in some sense, access control is ‘imperceptible’, and requires a lot of care to be set up properly. At the same time, improperly configured access control may easily jeopardize all other security instruments, as it would let the attacker walk in through the front door instead of squeezing through the window leaf or tearing down a (however protected) side wall.
The need-to-know principle, or the principle of least privilege, remains to be the most effective rule for setting up access rights correctly. To put it short, only give users access to information and functions they need to perform their duties – and forbid all the rest.