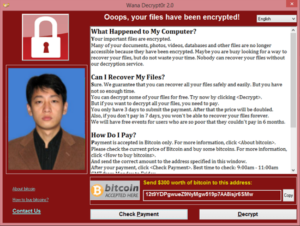
Last Thursday the US Department of Justice accused a North Korean hacker, Park Jin Hyok, of hacking Sony Pictures in 2014, committing a theft of $80m from the Bangladesh Central Bank in 2016, the launch of WannaCry malware in 2017, and a series of attacks on Lockheed Martin.
This is undoubtedly quite an impressive list of achievements for a single individual, especially taking into account education and career opportunities his country of residence is capable of providing.
Yet, there are two more thoughts about this matter that come to my mind.
First, it looks like a vast share of North Korean state hacking efforts had been concentrated in the hands of a single individual or a small group of individuals. Not only it is quite amusing to compare that, effectively, family business to some anthill-like underground syndicate carefully instilled in our heads by a crowd of politicians and journalists a good few orders of magnitude bigger; but it is also intriguing to speculate if we shall see the fall of the North Korean hacking programme now that Hyok is out of the game.
Second, all the above attacks have become known to us because they involved a straightforward and noticeable loss for their victims. However, a successful attack doesn’t always imply an immediate and tangible damage. Many hacks are performed by ‘black’ and ‘white’ enthusiasts doing that for all sorts of self-satisfaction; a lot are only performed to plant a time bomb and trigger it after a while; finally, a huge share of attacks target private and sensitive data stored at the victims’ premises, only to sell it later anonymously on dark web. All such attacks rarely get publicity. The bottom line here is, if a small group of NK hackers could do the damage of that scale, what is the actual potential of all the hackers out there?